- (Topic 23)
What is the correct order of steps in CEH System Hacking Cycle?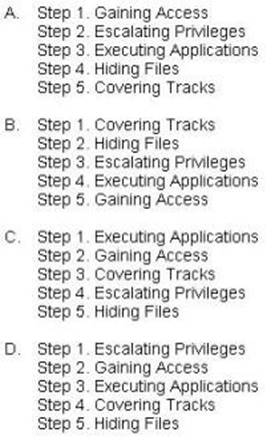
Correct Answer:
A
- (Topic 2)
Which of the following activities would not be considered passive footprinting?
Correct Answer:
C
Passive footprinting is a method in which the attacker never makes contact with the target. Scanning the targets IP addresses can be logged at the target and therefore contact has been made.
- (Topic 5)
What file system vulnerability does the following command take advantage of? type c:anyfile.exe > c:winntsystem32calc.exe:anyfile.exe
Correct Answer:
B
ADS (or Alternate Data Streams) is a “feature” in the NTFS file system that makes it possible to hide information in alternate data streams in existing files. The file can have multiple data streams and the data streams are accessed by filename:stream.
- (Topic 5)
Windows LAN Manager (LM) hashes are known to be weak. Which of the following are known weaknesses of LM? (Choose three)
Correct Answer:
ABD
The LM hash is computed as follows.1. The user’s password as an OEM string is converted to uppercase. 2. This password is either null-padded or truncated to 14 bytes. 3. The “fixed-length” password is split into two 7-byte halves. 4. These values are used to create two DES keys, one from each 7-byte half. 5. Each of these keys is used to DES-encrypt the constant ASCII string “KGS!@#$%”, resulting in two 8-byte ciphertext values. 6. These two ciphertext values are concatenated to form a 16-byte value, which is the LM hash.
The hashes them self are sent in clear text over the network instead of sending the password in clear text.
- (Topic 20)
Bob has a good understanding of cryptography, having worked with it for many years. Cryptography is used to secure data from specific threat, but it does not secure the application from coding errors. It can provide data privacy, integrity and enable strong authentication but it cannot mitigate programming errors.
What is a good example of a programming error that Bob can use to illustrate to the management that encryption will not address all of their security concerns?
Correct Answer:
C
A buffer overflow occurs when you write a set of values (usually a string of characters) into a fixed length buffer and write at least one value outside that buffer's boundaries (usually past its end). A buffer overflow can occur when reading input from the user into a buffer, but it can also occur during other kinds of processing in a program. Technically, a buffer overflow is a problem with the program's internal implementation.