- (Topic 19)
While examining a log report you find out that an intrusion has been attempted by a machine whose IP address is displayed as 0xde.0xad.0xbe.0xef. It looks to you like a hexadecimal number. You perform a ping 0xde.0xad.0xbe.0xef. Which of the following IP addresses will respond to the ping and hence will likely be responsible for the the intrusion?
Correct Answer:
E
Convert the hex number to binary and then to decimal.
0xde.0xad.0xbe.0xef translates to 222.173.190.239 and not 222.273.290.239
0xef = 15*1 = 15
14*16 = 224 = 239
= 239
0xbe = 14*1 = 14
11*16 = 176 = 190
= 190
0xad = 13*1 = 13
10*16 = 160 = 173
= 173
0xde = 14*1 = 14
13*16 = 208 = 222
= 222
- (Topic 23)
Steven is the senior network administrator for Onkton Incorporated, an oil well drilling company in Oklahoma City. Steven and his team of IT technicians are in charge of keeping inventory for the entire company; including computers, software, and oil well equipment. To keep track of everything, Steven has decided to use RFID tags on their entire inventory so they can be scanned with either a wireless scanner or a handheld scanner. These RFID tags hold as much information as possible about the equipment they are attached to. When Steven purchased these tags, he made sure they were as state of the art as possible. One feature he really liked was the ability to disable RFID tags if necessary. This comes in very handy when the company actually sells oil drilling equipment to other companies. All Steven has to do is disable the RFID tag on the sold equipment and it cannot give up any information that was previously stored on it.
What technology allows Steven to disable the RFID tags once they are no longer needed?
Correct Answer:
D
http://www.rsa.com/rsalabs/node.asp?id=2060
- (Topic 14)
Bank of Timbukut is a medium-sized, regional financial institution in Timbuktu. The bank has deployed a new Internet-accessible Web Application recently. Customers can access their account balances, transfer money between accounts, pay bills and conduct online financial business using a web browser.
John Stevens is in charge of information security at Bank of Timbukut. After one month in production, several customers have complained about the Internet enabled banking application. Strangely, the account balances of many of the bank’s customers had been changed ! However, money hasn’t been removed from the bank, instead money was transferred between accounts. Given this attack profile, John Stevens reviewed the Web Application’s logs and found the following entries.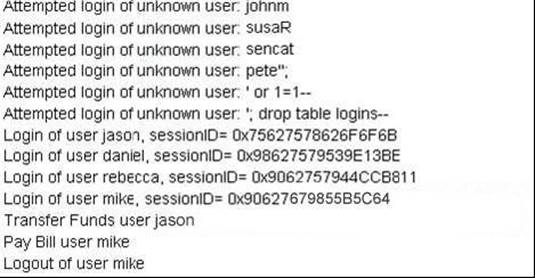
What kind of attack did the Hacker attempt to carry out at the Bank?
Correct Answer:
C
Typing things like ‘ or 1=1 – in the login field is evidence of a hacker trying out if the system is vulnerable to SQL injection.
- (Topic 14)
Identify SQL injection attack from the HTTP requests shown below:
Correct Answer:
C
The correct answer contains the code to alter the usertable in order to change the password for user smith to hAx0r
- (Topic 4)
Peter, a Network Administrator, has come to you looking for advice on a tool that would help him perform SNMP enquires over the network. Which of these tools would do the SNMP enumeration he is looking for?
Select the best answers.
Correct Answer:
ABD
Explanations:
SNMPUtil is a SNMP enumeration utility that is a part of the Windows 2000 resource kit. With SNMPUtil, you can retrieve all sort of valuable information through SNMP. SNScan is a SNMP network scanner by Foundstone. It does SNMP scanning to find open SNMP ports. Solarwinds IP Network Browser is a SNMP
enumeration tool with a graphical tree-view of the remote machine's SNMP data.