- (Topic 23)
Which of the following type of scanning utilizes automated process of proactively identifying vulnerabilities of the computing systems present on a network?
Correct Answer:
D
- (Topic 4)
Sara is using the nslookup command to craft queries to list all DNS information (such as Name Servers, host names, MX records, CNAME records, glue records (delegation for child Domains), zone serial number, TimeToLive (TTL) records, etc) for a Domain. What do you think Sara is trying to accomplish? Select the best answer.
Correct Answer:
B
The zone transfer is the method a secondary DNS server uses to update its information from the primary DNS server. DNS servers within a domain are organized using a master-slave method where the slaves get updated DNS information from the master DNS. One should configure the master DNS server to allow zone transfers only from secondary (slave) DNS servers but this is often not implemented. By connecting to a specific DNS server and successfully issuing the ls –d domain-name > file-name you have initiated a zone transfer.
- (Topic 19)
You are the security administrator for a large network. You want to prevent attackers
from running any sort of traceroute into your DMZ and discover the internal structure of publicly accessible areas of the network.
How can you achieve this?
Correct Answer:
D
When you run a traceroute to a target network address, you send a UDP packet with one time to live (TTL) to the target address. The first router this packet hits decreases the TTL to 0 and rejects the packet. Now the TTL for the packet is expired. The router sends back an ICMP message type 11 (Exceeded) code 0 (TTL--Exceeded) packet to your system with a source address. Your system displays the round-trip time for that first hop and sends out the next UDP packet with a TTL of 2.This process continues until you receive an ICMP message type 3 (Unreachable) code 3 (Port--Unreachable) from the destination system. Traceroute is completed when your machine receives a Port- Unreachable message.If you receive a message with three asterisks [* * *] during the traceroute, a router in the path doesn't return ICMP messages. Traceroute will continue to send UDP packets until the destination is reached or the maximum number of hops is exceeded.
- (Topic 7)
Exhibit: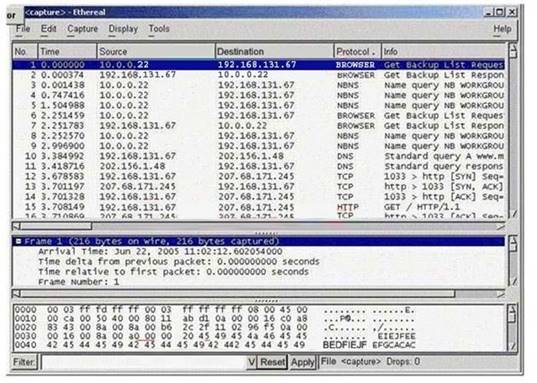
You have captured some packets in Ethereal. You want to view only packets sent from 10.0.0.22. What filter will you apply?
Correct Answer:
B
ip.src tells the filter to only show packets with 10.0.0.22 as the source.
- (Topic 23)
Wayne is the senior security analyst for his company. Wayne is examining some traffic logs on a server and came across some inconsistencies. Wayne finds some IP packets from a computer purporting to be on the internal network. The packets originate from
192.168.12.35 with a TTL of 15. The server replied to this computer and received a response from 192.168.12.35 with a TTL of 21. What can Wayne infer from this traffic log?
Correct Answer:
A