- (Topic 2)
Sam is working as a system administrator In an organization. He captured the principal characteristics of a vulnerability and produced a numerical score to reflect Its severity using CVSS v3.0 to property assess and prioritize the organization's vulnerability management processes. The base score that Sam obtained after performing cvss rating was 4.0. What is the CVSS severity level of the vulnerability discovered by Sam in the above scenario?
Correct Answer:
A
Rating CVSS Score None 0.0
Low 0.1 - 3.9
Medium 4.0 - 6.9
High 7.0 - 8.9
Critical 9.0 - 10.0
https://www.first.org/cvss/v3.0/specification-document
The Common Vulnerability Scoring System (CVSS) is an open framework for communicating the characteristics and severity of software vulnerabilities. CVSS consists of three metric groups: Base, Temporal, and Environmental. The Base metrics produce a score ranging from 0 to 10, which can then be modified by scoring the Temporal and Environmental metrics. A CVSS score is also represented as a vector string, a compressed textual representation of the values used to derive the score. Thus, CVSS is well suited as a standard measurement system for industries, organizations, and governments that need accurate and consistent vulnerability severity scores. Two common uses of CVSS are calculating the severity of vulnerabilities discovered on one's systems and as a factor in prioritization of vulnerability remediation activities. The National Vulnerability Database (NVD) provides CVSS scores for almost all known vulnerabilities.
Qualitative Severity Rating Scale
For some purposes, it is useful to have a textual representation of the numeric Base, Temporal and Environmental scores.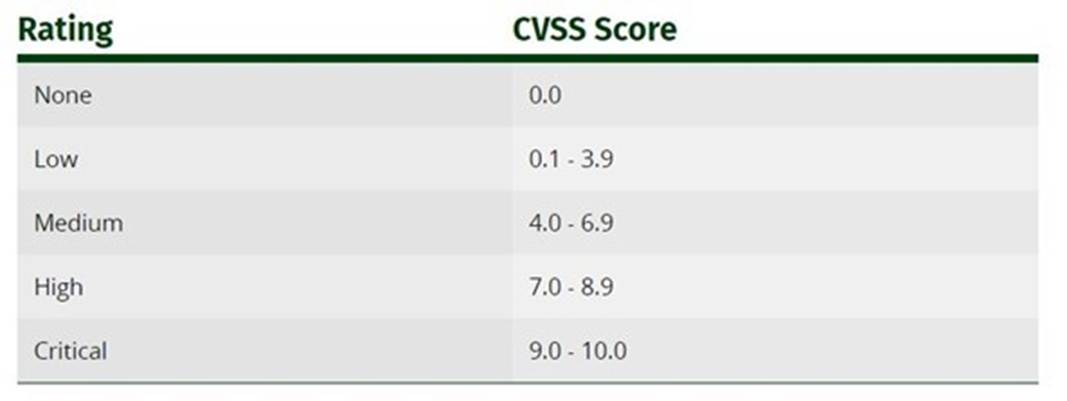
- (Topic 1)
A new wireless client is configured to join a 802.11 network. This client uses the same hardware and software as many of the other clients on the network. The client can see the network, but cannot connect. A wireless packet sniffer shows that the Wireless Access Point (WAP) is not responding to the association requests being sent by the wireless client. What is a possible source of this problem?
Correct Answer:
A
https://en.wikipedia.org/wiki/MAC_filtering
MAC filtering is a security method based on access control. Each address is assigned a 48-bit address, which is used to determine whether we can access a network or not. It helps in listing a set of allowed devices that you need on your Wi-Fi and the list of denied devices that you don??t want on your Wi-Fi. It helps in preventing unwanted access to the network. In a way, we can blacklist or white list certain computers based on their MAC address. We can configure the filter to allow connection only to those devices included in the white list. White lists provide greater security than blacklists because the router grants access only to selected devices.
It is used on enterprise wireless networks having multiple access points to prevent clients from communicating with each other. The access point can be configured only to allow clients to talk to the default gateway, but not other wireless clients. It increases the efficiency of access to a network.
The router allows configuring a list of allowed MAC addresses in its web interface, allowing you to choose which devices can connect to your network. The router has several functions designed to improve the network's security, but not all are useful. Media access control may seem advantageous, but there are certain flaws.
On a wireless network, the device with the proper credentials such as SSID and password can authenticate with the router and join the network, which gets an IP address and access to the internet and any shared resources.
MAC address filtering adds an extra layer of security that checks the device??s MAC address
against a list of agreed addresses. If the client??s address matches one on the router??s list, access is granted; otherwise, it doesn??t join the network.
- (Topic 3)
You are an ethical hacker contracted to conduct a security audit for a company. During the audit, you discover that the company's wireless network is using WEP encryption. You understand the vulnerabilities associated with WEP and plan to recommend a more secure encryption method. Which of the following would you recommend as a Suitable replacement to enhance the security of the company's wireless network?
Correct Answer:
B
WEP encryption is an outdated and insecure method of protecting wireless networks from unauthorized access and eavesdropping. WEP uses a static key that can be easily cracked by various tools and techniques, such as capturing the initialization vectors, brute-forcing the key, or exploiting the weak key scheduling algorithm1. Therefore, you should recommend a more secure encryption method to enhance the security of the company??s wireless network.
One of the most suitable replacements for WEP encryption is WPA2-PSK with AES encryption. WPA2 stands for Wi-Fi Protected Access 2, which is a security standard that improves upon the previous WPA standard. WPA2 uses a robust encryption algorithm called AES, which stands for Advanced Encryption Standard. AES is a block cipher that uses a 128-bit key and is considered to be very secure and resistant to attacks2.
WPA2-PSK stands for WPA2 Pre-Shared Key, which is a mode of WPA2 that uses a passphrase or a password to generate the encryption key. The passphrase or password must be entered by the users who want to connect to the wireless network. The key is then derived from the passphrase or password using a function called PBKDF2, which stands for Password-Based Key Derivation Function 2. PBKDF2 adds a salt and a number of iterations to the passphrase or password to make it harder to crack3.
WPA2-PSK with AES encryption offers several advantages over WEP encryption, such as:
✑ It uses a dynamic key that changes with each session, instead of a static key that remains the same.
✑ It uses a stronger encryption algorithm that is more difficult to break, instead of a weaker encryption algorithm that is more vulnerable to attacks.
✑ It uses a longer key that provides more security, instead of a shorter key that provides less security.
✑ It uses a more secure key derivation function that adds complexity and randomness, instead of a simple key generation function that is predictable and flawed.
Therefore, you should recommend WPA2-PSK with AES encryption as a suitable replacement to enhance the security of the company??s wireless network. References:
✑ Wireless Security - Encryption - Online Tutorials Library
✑ WiFi Security: WEP, WPA, WPA2, WPA3 And Their Differences - NetSpot
✑ WPA2-PSK (Wi-Fi Protected Access 2 Pre-Shared Key)
- (Topic 3)
As a security analyst for Sky Secure Inc., you are working with a client that uses a multi- cloud strategy, utilizing services from several cloud providers. The client wants to implement a system that will provide unified security management across all their cloud platforms. They need a solution that allows them to consistently enforce security policies, identify and respond to threats, and maintain visibility of all their cloud resources. Which of the following should you recommend as the best solution?
Correct Answer:
C
A Cloud Access Security Broker (CASB) is a security policy enforcement point, either on-premises or in the cloud, that administers an organization??s enterprise security policies when users attempt to access its cloud-based resources. A CASB can provide unified security management across multiple cloud platforms, as it can monitor cloud activity, enforce security policies, identify and respond to threats, and maintain visibility of all cloud resources. A CASB can also integrate with other security tools, such as data loss prevention (DLP), encryption, malware detection, and identity and access management (IAM), to enhance the security posture of the organization.
The other options are not as effective or feasible as using a CASB. Using a hardware- based firewall to secure all cloud resources may not be compatible with the dynamic and scalable nature of the cloud, as it may introduce latency, complexity, and cost. Implementing separate security management tools for each cloud platform may create inconsistency, inefficiency, and confusion, as each tool may have different features, interfaces, and configurations. Relying on the built-in security features of each cloud platform may not be sufficient or comprehensive, as each platform may have different levels of security, compliance, and functionality. References:
✑ What Is a Cloud Access Security Broker (CASB)? | Microsoft
✑ What Is a CASB? - Cloud Access Security Broker - Cisco
✑ What is a Cloud Access Security Broker (CASB)?
- (Topic 3)
Which tier in the N-tier application architecture is responsible for moving and processing data between the tiers?
Correct Answer:
C