Refer to the exhibit.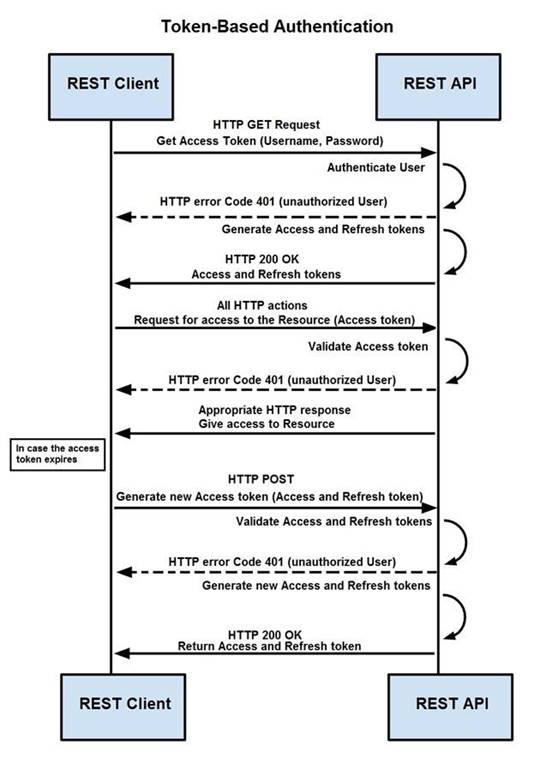
How are tokens authenticated when the REST API on a device is accessed from a REST API client?
Correct Answer:
D
Refer to the exhibit.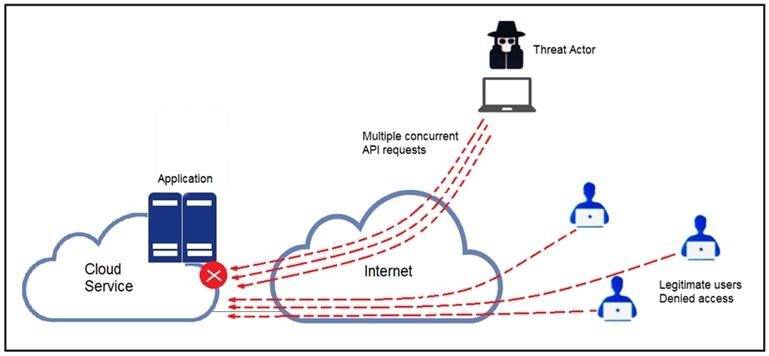
A threat actor behind a single computer exploited a cloud-based application by sending multiple concurrent API requests. These requests made the application unresponsive. Which solution protects the application from being overloaded and ensures more equitable application access across the end-user community?
Correct Answer:
A
Refer to the exhibit.
IDS is producing an increased amount of false positive events about brute force attempts on the organization’s mail server. How should the Snort rule be modified to improve performance?
Correct Answer:
B
An organization installed a new application server for IP phones. An automated process fetched user credentials from the Active Directory server, and the application will have access to on-premises and cloud services. Which security threat should be mitigated first?
Correct Answer:
B
An engineer notices that unauthorized software was installed on the network and discovers that it was installed by a dormant user account. The engineer suspects an escalation of privilege attack and responds to the incident. Drag and drop the activities from the left into the order for the response on the right.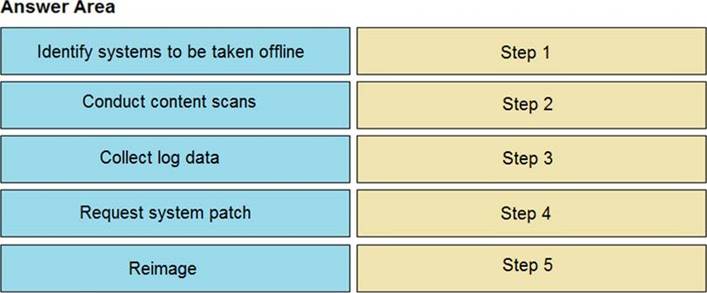
Solution: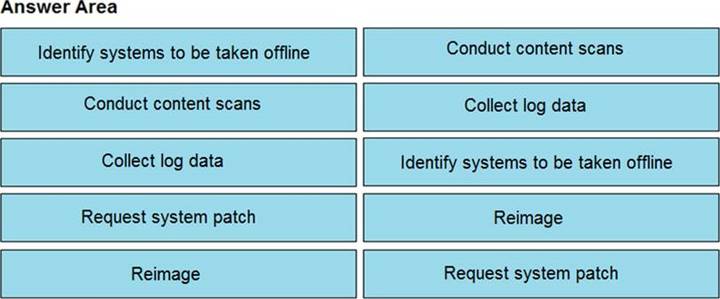
Does this meet the goal?
Correct Answer:
A