A company has hired a security architect to address several service outages on the endpoints due to new malware. The Chief Executive Officer’s laptop was impacted while working from home. The goal is to prevent further endpoint disruption. The edge network is protected by a web proxy.
Which of the following solutions should the security architect recommend?
Correct Answer:
A
Replacing the current antivirus with an EDR (endpoint detection and response) solution is the best solution for addressing several service outages on the endpoints due to new malware. An EDR solution is a technology that provides advanced capabilities for detecting, analyzing, and responding to threats or incidents on endpoints, such as computers, laptops, mobile devices, or servers. An EDR solution can use behavioral analysis, machine learning, threat intelligence, or other methods to identify new or unknown malware that may evade traditional antivirus solutions. An EDR solution can also provide automated or manual remediation actions, such as isolating, blocking, or removing malware from endpoints. Removing the web proxy and installing a UTM (unified threat management) appliance is not a good solution for addressing service outages on endpoints due to new malware, as it could expose endpoints to more threats or attacks by removing a layer of protection that filters web traffic, as well as not provide sufficient detection or response capabilities for endpoint-specific malware. Implementing a deny list feature on endpoints is not a good solution for addressing service outages on endpoints due to new malware, as it could be ineffective or impractical for blocking new or unknown malware that may not be on the deny list, as well as not provide sufficient detection or response capabilities for endpoint-specific malware. Adding a firewall module on the current antivirus solution is not a good solution for addressing service outages on endpoints due to new malware, as it could introduce compatibility or performance issues for endpoints by adding an additional feature that may not be integrated or optimized with the antivirus solution, as well as not provide sufficient detection or response capabilities for endpoint-specific malware. Verified References: https://www.comptia.org/blog/what-is-edr https://partners.comptia.org/docs/default-source/resources/casp-content-guide
An auditor Is reviewing the logs from a web application to determine the source of an Incident. The web application architecture Includes an Internet-accessible application load balancer, a number of web servers In a private subnet, application servers, and one database server In a tiered configuration. The application load balancer cannot store the logs. The following are sample log snippets: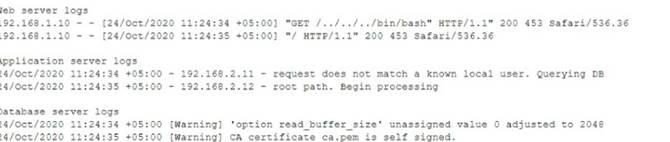
Which of the following should the auditor recommend to ensure future incidents can be traced back to the sources?
Correct Answer:
C
An application server was recently upgraded to prefer TLS 1.3, and now users are unable to connect their clients to the server. Attempts to reproduce the error are confirmed, and clients are reporting the following:
ERR_SSL_VERSION_OR_CIPHER_MISMATCH
Which of the following is MOST likely the root cause?
Correct Answer:
C
Reference: https://kinsta.com/knowledgebase/err_ssl_version_or_cipher_mismatch/
The client application being configured to use RC4 is the most likely root cause of why users are unable to connect their clients to the server that prefers TLS 1.3. RC4 is an outdated and insecure symmetric-key encryption algorithm that has been deprecated and removed from TLS 1.3, which is the latest version of the protocol that provides secure communication between clients and servers. If the client application is configured to use RC4, it will not be able to negotiate a secure connection with the server that prefers TLS 1.3, resulting in an error message such as ERR_SSL_VERSION_OR_CIPHER_MISMATCH. The client application testing PFS (perfect forward secrecy) is not a likely root cause of why users are unable to connect their clients to the server that prefers TLS 1.3, as PFS is a property that ensures that session keys derived from a set of long-term keys cannot be compromised if one of them is compromised in the future. PFS is supported and recommended by TLS 1.3, which uses ephemeral Diffie-Hellman or elliptic curve Diffie-Hellman key exchange methods to achieve PFS. The client application being configured to use ECDHE (elliptic curve Diffie-Hellman ephemeral) is not a likely root cause of why users are unable to connect their clients to the server that prefers TLS 1.3, as ECDHE is a key exchange method that provides PFS and high performance by using elliptic curve cryptography to generate ephemeral keys for each session. ECDHE is supported and recommended by TLS 1.3, which uses ECDHE as the default key exchange method. The client application being configured to use AES-256 in GCM (Galois/Counter Mode) is not a likely root cause of why users are unable to connect
their clients to the server that prefers TLS 1.3, as AES-256 in GCM is an encryption mode that provides confidentiality and integrity by using AES with a 256-bit key and GCM as an authenticated encryption mode. AES-256 in GCM is supported and recommended by TLS 1.3, which uses AES-256 in GCM as one of the default encryption modes. Verified References: https://www.comptia.org/blog/what-is-tls-13 https://partners.comptia.org/docs/default-source/resources/casp-content-guide
An organization is preparing to migrate its production environment systems from an on- premises environment to a cloud service. The lead security architect is concerned that the organization's current methods for addressing risk may not be possible in the cloud environment.
Which of the following BEST describes the reason why traditional methods of addressing risk may not be possible in the cloud?
Correct Answer:
C
According to NIST SP 800-146, cloud computing introduces new risks that need to be assessed and managed by the cloud consumer. Some of these risks are related to the shared responsibility model of cloud computing, where some security controls are implemented by the cloud provider and some by the cloud consumer. The cloud consumer cannot transfer all the risks to the cloud provider and needs to understand which risks are retained and which are mitigated by the cloud provider.3
Which of the following BEST describes a common use case for homomorphic encryption ?
Correct Answer:
C
Homomorphic encryption is a type of encryption method that allows computations to be performed on encrypted data without first decrypting it with a secret key. The results of the computations also remain encrypted and can only be decrypted by the owner of the private key. Homomorphic encryption can be used for privacy-preserving outsourced storage and computation. This means that data can be encrypted and sent to a cloud service provider (CSP) for processing, without revealing any information to the CSP or anyone else who might intercept the data. Homomorphic encryption can enable new services and applications that require processing confidential data on a large number of resources, such as machine learning, data analytics, health care, finance, and voting.
* A. Processing data on a server after decrypting in order to prevent unauthorized access in transit is not a common use case for homomorphic encryption, because it does not take advantage of the main feature of homomorphic encryption, which is computing over encrypted data. This use case can be achieved by using any standard encryption method that provides confidentiality for data in transit.
* B. Maintaining the confidentiality of data both at rest and in transit to and from a CSP for processing is not a common use case for homomorphic encryption, because it does not take advantage of the main feature of homomorphic encryption, which is computing over encrypted data. This use case can be achieved by using any standard encryption method that provides confidentiality for data at rest and in transit.
* D. Storing proprietary data across multiple nodes in a private cloud to prevent access by unauthenticated users is not a common use case for homomorphic encryption, because it does not involve any computation over encrypted data. This use case can be achieved by using any standard encryption method that provides confidentiality for data at rest.
https://www.splunk.com/en_us/blog/learn/homomorphic-encryption.html https://research.aimultiple.com/homomorphic-encryption/