Which of the following are the MOST likely reasons lo include reporting processes when updating an incident response plan after a breach? (Select TWO).
Correct Answer:
BC
Reporting processes are important to include when updating an incident response plan after a breach for several reasons. Two of the most likely reasons are: To meet regulatory requirements for timely reporting. Many regulations and standards require organizations to report security incidents or breaches within a certain time frame or face penalties or sanctions. For example, the General Data Protection Regulation (GDPR) requires organizations to report personal data breaches within 72 hours of becoming aware of them. Reporting processes can help organizations to comply with these requirements by defining who, what, when, where, how, and why to report incidents or breaches.
To meet regulatory requirements for timely reporting. Many regulations and standards require organizations to report security incidents or breaches within a certain time frame or face penalties or sanctions. For example, the General Data Protection Regulation (GDPR) requires organizations to report personal data breaches within 72 hours of becoming aware of them. Reporting processes can help organizations to comply with these requirements by defining who, what, when, where, how, and why to report incidents or breaches. To limit reputation damage caused by the breach. Security incidents or breaches can have negative impacts on an organization’s reputation, trust, and customer loyalty. Reporting processes can help organizations to limit these impacts by communicating effectively and transparently with internal and external stakeholders, such as employees, customers, partners, regulators, media, and public. Reporting processes can help organizations to provide accurate and consistent information about the breach, its causes, impacts, and remediation actions.
To limit reputation damage caused by the breach. Security incidents or breaches can have negative impacts on an organization’s reputation, trust, and customer loyalty. Reporting processes can help organizations to limit these impacts by communicating effectively and transparently with internal and external stakeholders, such as employees, customers, partners, regulators, media, and public. Reporting processes can help organizations to provide accurate and consistent information about the breach, its causes, impacts, and remediation actions.
Other possible reasons to include reporting processes when updating an incident response plan after a breach are: To establish a clear chain of command (A). Reporting processes can help organizations to establish a clear chain of command for incident response by defining roles and responsibilities, escalation procedures, and decision-making authority.
To establish a clear chain of command (A). Reporting processes can help organizations to establish a clear chain of command for incident response by defining roles and responsibilities, escalation procedures, and decision-making authority. To remediate vulnerabilities that led to the breach (D). Reporting processes can help organizations to remediate vulnerabilities that led to the breach by documenting and analyzing the root causes, lessons learned, and best practices for improvement.
To remediate vulnerabilities that led to the breach (D). Reporting processes can help organizations to remediate vulnerabilities that led to the breach by documenting and analyzing the root causes, lessons learned, and best practices for improvement. To isolate potential insider threats (E). Reporting processes can help organizations to isolate potential insider threats by monitoring and auditing user activities, behaviors, and access rights before, during, and after the breach.
To isolate potential insider threats (E). Reporting processes can help organizations to isolate potential insider threats by monitoring and auditing user activities, behaviors, and access rights before, during, and after the breach.
References: : https://gdpr.eu/data-breach-notification/ : https://www.techopedia.com/definition/13493/penetration-testing : https://www.techopedia.com/definition/25888/security-development-lifecycle-sdl
A company is aiming to test a new incident response plan. The management team has made it clear that the initial test should have no impact on the environment. The company has limited
resources to support testing. Which of the following exercises would be the best approach?
Correct Answer:
A
A tabletop scenario is an informal, discussion-based session in which a team discusses their roles and responses during an emergency, walking through one or more example scenarios. A tabletop scenario is the best approach for a company that wants to test a new incident response plan without impacting the environment or using many resources. A tabletop scenario can help the company identify strengths and weaknesses in their plan, clarify roles and responsibilities, and improve communication and coordination among team members. The other options are more intensive and disruptive exercises that involve simulating a real incident or attack. References: CompTIA Cybersecurity Analyst (CySA+) Certification Exam Objectives (CS0-002), page 16; https://www.linkedin.com/pulse/tabletop-exercises-explained-matt-lemon-phd
A security analyst found an old version of OpenSSH running on a DMZ server and determined the following piece of code could have led to a command execution through an integer overflow;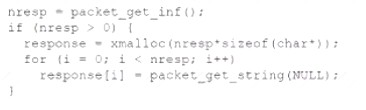
Which of the following controls must be in place to prevent this vulnerability?
Correct Answer:
C
The security analyst should implement a control that uses built-in functions from libraries to check and handle long numbers properly. This will help prevent integer overflow vulnerabilities, which occur when a value is moved into a variable type too small to hold it. For example, if an integer variable can only store values up to 255, and a value of 256 is assigned to it, the variable will overflow and wrap around to 0. This can cause unexpected program behavior or lead to buffer overflow vulnerabilities if the overflowed value is used as an index or size for memory allocation1. Built-in functions from libraries can help avoid integer overflow by performing checks on the input values and the resulting values, and throwing exceptions or errors if they exceed the limits of the variable type2.
A security analyst sees the following OWASP ZAP output from a scan that was performed against a modern version of Windows while testing for client-side vulnerabilities: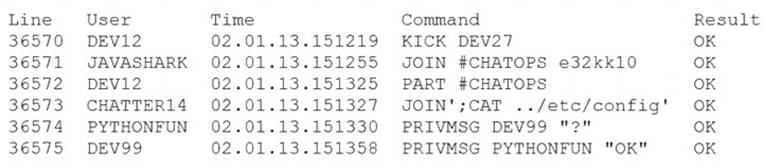
Which of the following is the MOST likely solution to the listed vulnerability?
Correct Answer:
A
Enabling the browser’s XSS filter would be the most likely solution to the listed vulnerability. The vulnerability is a reflected cross-site scripting (XSS) attack, which occurs when a malicious script is injected into a web page that reflects user input back to the browser without proper validation or encoding. The malicious script can then execute in the browser and perform various actions, such as stealing cookies, redirecting to malicious sites, or displaying fake content2. Enabling the browser’s XSS filter can help prevent reflected XSS attacks by detecting and blocking malicious scripts before they execute in the browser3.
A security analyst is looking at the headers of a few emails that appear to be targeting all users at an organization: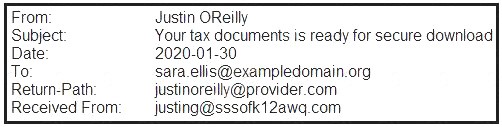
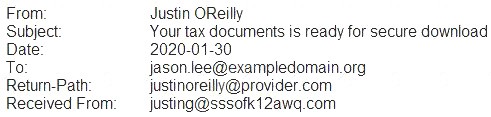
Which of the following technologies would MOST likely be used to prevent this phishing attempt?
Correct Answer:
B
DMARC stands for Domain-based Message Authentication, Reporting and Conformance. It is an email authentication protocol that helps prevent spoofing and phishing attacks by verifying that the sender’s domain matches the domain in the email header. DMARC also provides a way for domain owners to specify how receivers should handle unauthenticated messages from their domain1