Which of the following is a vulnerability associated with the Modbus protocol?
Correct Answer:
D
Modbus is a communication protocol that is widely used in industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems. However, Modbus was not designed to provide security and it is vulnerable to various cyberattacks. One of the main vulnerabilities of Modbus is the lack of authentication, which means that any device on the network can send or receive commands without verifying its identity or authority. This can lead to unauthorized access, data manipulation, or denial of service attacks on the ICS or SCADA system.
Some examples of attacks that exploit the lack of authentication in Modbus are: Detection attack: An attacker can scan the network and discover the devices and their addresses, functions, and registers by sending Modbus requests and observing the responses. This can reveal sensitive information about the system configuration and operation1.
Detection attack: An attacker can scan the network and discover the devices and their addresses, functions, and registers by sending Modbus requests and observing the responses. This can reveal sensitive information about the system configuration and operation1. Command injection attack: An attacker can send malicious commands to the devices and modify their settings, values, or outputs. For example, an attacker can change the speed of a motor, open or close a valve, or turn off a switch23.
Command injection attack: An attacker can send malicious commands to the devices and modify their settings, values, or outputs. For example, an attacker can change the speed of a motor, open or close a valve, or turn off a switch23. Response injection attack: An attacker can intercept and alter the responses from the devices and
Response injection attack: An attacker can intercept and alter the responses from the devices and
deceive the master or other devices about the true state of the system. For example, an attacker can fake a normal response when there is an error or an alarm23. Denial of service attack: An attacker can flood the network with Modbus requests or commands and overload the devices or the communication channel. This can prevent legitimate requests or commands from being processed and disrupt the normal operation of the system14.
Denial of service attack: An attacker can flood the network with Modbus requests or commands and overload the devices or the communication channel. This can prevent legitimate requests or commands from being processed and disrupt the normal operation of the system14.
To mitigate these attacks, some security measures that can be applied to Modbus are: Encryption: Encrypting the Modbus messages can prevent eavesdropping and tampering by unauthorized parties. However, encryption can also introduce additional overhead and latency to the communication56.
Encryption: Encrypting the Modbus messages can prevent eavesdropping and tampering by unauthorized parties. However, encryption can also introduce additional overhead and latency to the communication56. Authentication: Adding authentication mechanisms to Modbus can ensure that only authorized devices can send or receive commands. Authentication can be based on passwords, certificates, tokens, or other methods56.
Authentication: Adding authentication mechanisms to Modbus can ensure that only authorized devices can send or receive commands. Authentication can be based on passwords, certificates, tokens, or other methods56. Firewall: Installing a firewall between the Modbus network and other networks can filter out unwanted traffic and block unauthorized access. A firewall can also enforce rules and policies for Modbus communication24.
Firewall: Installing a firewall between the Modbus network and other networks can filter out unwanted traffic and block unauthorized access. A firewall can also enforce rules and policies for Modbus communication24. Intrusion detection system: Deploying an intrusion detection system (IDS) on the Modbus network can monitor the traffic and detect anomalous or malicious activities. An IDS can also alert the operators or trigger countermeasures when an attack is detected24.
Intrusion detection system: Deploying an intrusion detection system (IDS) on the Modbus network can monitor the traffic and detect anomalous or malicious activities. An IDS can also alert the operators or trigger countermeasures when an attack is detected24.
During the onboarding process for a new vendor, a security analyst obtains a copy of the vendor's latest penetration test summary: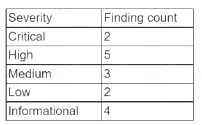
Performed by: Vendor Red Team Last performed: 14 days ago
Which of the following recommendations should the analyst make first?
Correct Answer:
C
The analyst should disclose details regarding the findings of the vendor’s latest penetration test summary as the first recommendation, as this can help assess the vendor’s security posture and identify any potential risks or issues that may affect the organization. The analyst should review the findings and ask for more information about the scope, methodology, and remediation actions of the penetration test, as well as any evidence or artifacts that support the findings.
Which of the following ICS network protocols has no inherent security functions on TCP port 502?
Correct Answer:
D
Modbus is an industrial control system (ICS) network protocol that is used for communication between devices such as sensors, controllers, actuators, and monitors. Modbus has no inherent security functions on TCP port 502, which is the default port for Modbus TCP/IP communication. Modbus does not provide any encryption, authentication, or integrity protection for the data transmitted over the network, making it vulnerable to various attacks such as replay, modification, spoofing, or denial-of-service.
A security analyst reviews SIEM logs and discovers the following error event: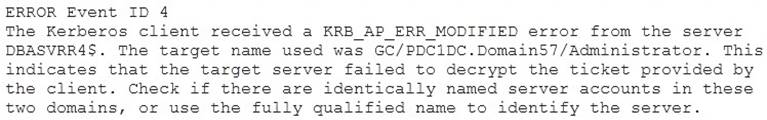
Which of the following environments does the analyst need to examine to continue troubleshooting the event?
Correct Answer:
C
A Windows domain controller is a server that manages authentication and authorization for users and computers in a Windows domain. A Windows domain controller uses Active Directory Domain Services (AD DS) to store information about users, groups, computers, policies, and other objects in a domain. A Windows domain controller can generate event logs that record various activities and events related to security, system, application, etc. The event log shown in the question indicates that it was generated by a Windows domain controller with an IP address of 10.0.0.1 and a hostname of DC01.
Company A is m the process of merging with Company B As part of the merger, connectivity between the ERP systems must be established so portent financial information can be shared between the two entitles. Which of the following will establish a more automated approach to secure data transfers between the two entities?
Correct Answer:
C
The security analyst should set up a PKI (Public Key Infrastructure) between Company A and Company B and exchange shared certificates between the two entities. This will allow them to establish a more automated approach to secure data transfers between their ERP systems. A PKI is a system that provides encryption and authentication services using public key cryptography. A PKI consists of certificates, certificate authorities (CAs), and other components that enable users to securely exchange data over untrusted networks. By exchanging shared certificates between Company A and Company B, they can verify each other’s identity and encrypt their data using public and private keys.