- (Topic 4)
A corporation is evaluating an offer from a CSP to take advantage of volume discounts on a shared platform. The finance department is concerned about cost allocation transparency, as the current structure splits projects into dedicated billing accounts. Which of the following can be used to address this concern?
Correct Answer:
A
Resource tagging is a process of adding descriptive metadata (tags) to cloud resources, such as virtual machines, storage accounts, databases, etc. Tags can be used to track and allocate costs, identify resources by project, owner, environment, or any other criteria. Resource tagging can help the finance department to have cost allocation transparency across different projects on a shared platform. References: CompTIA Cloud+ Certification Exam Objectives, Domain 4.0: Operations and Support, Objective 4.3: Given a scenario, apply the appropriate methods for cost control in a cloud environment. Cloud Resource Tagging | Cloud Foundation Community, Define your tagging strategy - Cloud Adoption Framework
- (Topic 1)
A SAN that holds VM files is running out of storage space.
Which of the following will BEST increase the amount of effective storage on the SAN?
Correct Answer:
D
Deduplication is a type of data compression technique that eliminates redundant or duplicate data blocks or segments in a storage system or device. Configuring deduplication can help increase the amount of effective storage on a SAN that holds VM files and is running out of storage space, as it can reduce the storage space consumption and increase the storage space utilization by storing only unique data blocks or segments. Configuring deduplication can also improve performance and efficiency, as it can speed up data transfer and backup processes and save network bandwidth and power consumption. References: CompTIA Cloud+ Certification Exam Objectives, page 9, section 1.4
- (Topic 2)
Which of the following will provide a systems administrator with the MOST information about potential attacks on a cloud IaaS instance?
Correct Answer:
D
HIDS (Host-based Intrusion Detection System) is the tool that will provide the administrator with the most information about potential attacks on a cloud IaaS instance. HIDS is a software or agent that monitors and analyzes the activities and events on a host system or device, such as a cloud instance. HIDS can detect and alert on any malicious or anomalous behavior, such as unauthorized access, malware infection, configuration changes, etc., that may indicate an attack or compromise.
- (Topic 4)
An application deployment team has observed delays in deployments and has asked the cloud administrator to evaluate the issue. Below is the result of a latency test that was conducted by the cloud administrator from offices located in the following regions:
• Asia-Pacific (APAC)
• Europe, the Middle East, and Africa (EMEA)
• Americas
Tests were conducted from each location, and the results are shown below: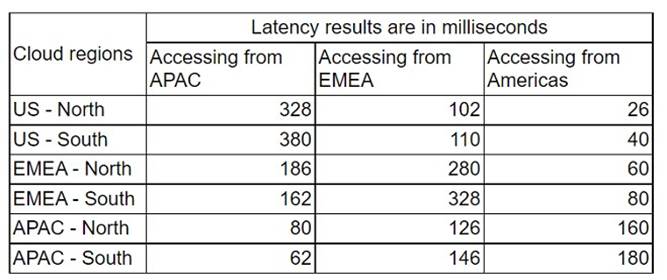
Which of the following locations needs to be investigated further?
Correct Answer:
D
The latency test results show that the connectivity from APAC to EMEA and Americas regions has the highest latency values, ranging from 162 ms to 380 ms. This indicates that there is a significant delay in the network communication between these regions, which could affect the performance and availability of the cloud services. The connectivity from EMEA to all regions also has high latency values, ranging from 60 ms to 328 ms, which could also cause issues for the application deployment team. Therefore, these locations need to be investigated further to identify and resolve the root cause of the network latency.
Some possible causes of network latency are :
✑ Congestion: The network bandwidth may be insufficient to handle the volume of traffic, resulting in packet loss, retransmission, and queuing delays.
✑ Distance: The physical distance between the source and destination nodes may increase the propagation delay, which is the time it takes for a signal to travel through a medium.
✑ Routing: The network topology and configuration may affect the number and quality of hops that a packet takes to reach its destination, resulting in transmission and processing delays.
✑ Hardware: The performance and capacity of the network devices, such as routers, switches, firewalls, and servers, may affect the speed and efficiency of data processing and delivery.
Some possible solutions to reduce network latency are :
✑ Scaling: The network resources can be increased or optimized to handle the traffic demand, such as adding more bandwidth, load balancers, or caching servers.
✑ Location: The network nodes can be placed closer to each other or to the end users, such as using edge computing, content delivery networks (CDNs), or regional cloud data centers.
✑ Routing: The network routes can be improved or optimized to reduce the number and distance of hops, such as using direct peering, dedicated circuits, or software- defined networking (SDN).
✑ Hardware: The network devices can be upgraded or replaced with faster and more reliable ones, such as using solid-state drives (SSDs), fiber-optic cables, or 5G technology.
References:
What is Network Latency? | Cloudflare
How To Reduce Network Latency In 2021 - DNSstuff
- (Topic 3)
A systems administrator needs to modify the replication factors of an automated application container from 3 to 5. Which of the following file types should the systems administrator modify on the master controller?
Correct Answer:
A
A .yaml file is a common file type for defining the configuration and deployment of application containers in a cloud environment. YAML stands for YAML Ain’t Markup Language, and it is a human-readable data serialization language that uses indentation and keywords to represent the structure and values of the data1. A .yaml file can specify the properties of the container, such as the image, ports, environment variables, volumes, resources, and scaling rules. For example, to modify the replication factor of an automated application container from 3 to 5, the systems administrator can edit the .yaml file on the master controller and change the value of the replicas field under the spec section2. For example:
apiVersion: apps/v1 kind: Deployment metadata: name: my-app spec: replicas: 5 # change this value from 3 to 5 selector: matchLabels: app: my-app template: metadata: labels: app: my-app spec: containers: - name: my-app image: my-app-image ports: - containerPort: 80 A .txt file is a plain text file that can store any kind of text data, but it is not a standard format for defining container configurations. A .conf file is a configuration file that can store settings and parameters for various applications or services, but it is not commonly used for container deployments. A .etcd file is not a valid file type, but etcd is a distributed key- value store that provides a reliable way to store data across a cluster of machines3. Etcd is often used by Kubernetes, a popular platform for managing containerized applications, to store and synchronize the cluster state. However, etcd does not store the configuration files of the containers, but rather the runtime data of the cluster. Therefore, none of these options are correct.