A cloud engineer wants containers to run the latest version of a container base image to reduce the number of vulnerabilities. The applications in use requite Python 3.10 and ate not compatible with any other version. The containers' images are created every time a new version is released from the source image. Given the container Dockerfile below: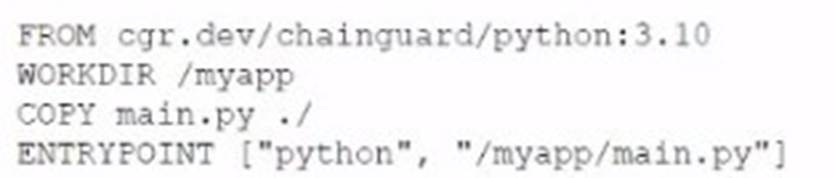
Which of the following actions will achieve the objectives with the least effort?
Correct Answer:
A
Performing a "docker pull" before executing "docker run" ensures that the latest version of the container base image is used, aligning with the objective of reducing vulnerabilities. This command fetches the latest image version from the repository, ensuring that the container runs the most up-to-date and secure version of the base image. This approach is efficient and requires minimal effort, as it automates the process of maintaining the latest image versions for container deployments.References: Within the CompTIA Cloud+ examination scope, understanding management and technical operations in cloud environments, including container management and security, is critical. This includes best practices for maintaining up-to-date container images to minimize vulnerabilities.
Which of the following network protocols is generally used in a NAS environment?
Correct Answer:
C
The network protocol generally used in a NAS (Network Attached Storage) environment is TCP/IP (Transmission Control Protocol/Internet Protocol). NAS devices are accessed over a network rather than being directly connected to the computer, and they utilize the TCP/IP protocol to enable this network communication.References: Understanding of networking protocols, including TCP/IP in the context of NAS environments, is part of the foundational networking knowledge for cloud services in CompTIA Cloud+.
A company experienced a data leak through its website. A security engineer, who is investigating the issue, runs a vulnerability scan against the website and receives the following output: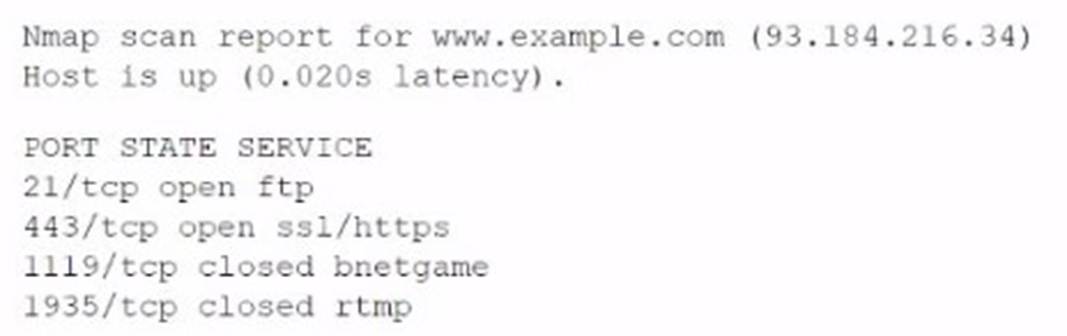
Which of the following is the most likely cause of this leak?
Correct Answer:
D
The data leak is most likely caused by the use of an insecure protocol. The vulnerability scan output shows that port 21/tcp for FTP (File Transfer Protocol) is open. FTP is known for transmitting data unencrypted, which could allow sensitive data to be intercepted during transfer.References: The security risks associated with the use of insecure or unencrypted protocols are covered under cloud security best practices in the CompTIA Cloud+ curriculum.
A cloud engineer is running a latency-sensitive workload that must be resilient and highly available across multiple regions. Which of the following concepts best addresses these
requirements?
Correct Answer:
B
Clustering refers to the use of multiple servers/computers to form what appears to be a single system. This concept is key for achieving high availability and resilience, especially for latency-sensitive workloads. By distributing the workload across a cluster that spans multiple regions, the system can continue to operate even if one or more nodes fail, thus maintaining performance and availability. References: CompTIA Cloud+ Guide to Cloud Computing (ISBN: 978-1-64274-282-2)
Which of the following vulnerability management concepts is best defined as the process of discovering vulnerabilities?
Correct Answer:
D
In vulnerability management, 'Identification' is the concept best defined as the process of discovering vulnerabilities. This step is crucial as it involves detecting vulnerabilities in systems, software, and networks, which is the first step in the vulnerability management process before moving on to assessment, remediation, and reporting.