- (Exam Topic 3)
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE Each correct selection is worth one point.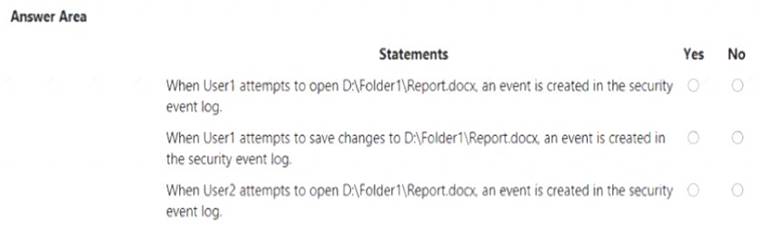
Solution: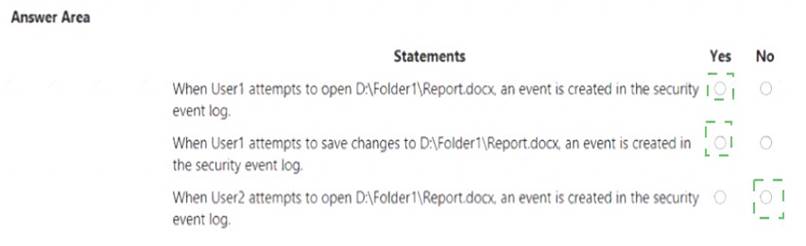
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have two computers named Computer1 and Computer2 that run Windows 10.
You have an Azure Active Directory (Azure AD) user account named admin@contoso.com that is in the local Administrators group on each computer.
You sign in to Computer1 by using admin@contoso.com.
You need to ensure that you can use Event Viewer on Computer1 to connect to the event logs on Computer2. Solution: On Computer2, you enable the Remote Event Log Management inbound rule from Windows
Defender Firewall.
Does this meet the goal?
Correct Answer:
A
Reference:
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc76643
- (Exam Topic 4)
You have a Windows 10 device named Device1.
You plan purchase a wireless display device that will stream audio and video from Device1. Which wireless feature or protocol should the display device support?
Correct Answer:
B
- (Exam Topic 4)
You have a computer named Computer1 that runs Windows 10. Computer1 has a folder named C:Folder1.
You need to meet the following requirements:  Log users that access C:Folder1.
Log users that access C:Folder1. Log users that modify and delete files in C:Folder1. Which two actions should you perform?
Log users that modify and delete files in C:Folder1. Which two actions should you perform?
Correct Answer:
AD
Files and folders are objects and are audited through object access. Reference:
https://www.netwrix.com/how_to_detect_who_changed_file_or_folder_owner.html
- (Exam Topic 4)
You have a computer named Computer 1 that runs Windows 10.
You turn on System Protection and create a restore point named Point1. You perform the following changes: Add four files named File1.txt, File2.dll, File3.sys, and File4.exe to the desktop. Run a configuration script that adds the following four registry keys:
Add four files named File1.txt, File2.dll, File3.sys, and File4.exe to the desktop. Run a configuration script that adds the following four registry keys:
- Key1 to HKEY_CURRENT_USER
- Key2 to HKEY_CLASSES_ROOT
- Key3 to HKEY_LOCAL_MACHINESYSTEM
- Key4 to HKEY_CURRENT_CONFIG
You restore Point1.
Which files and registry keys are removed? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.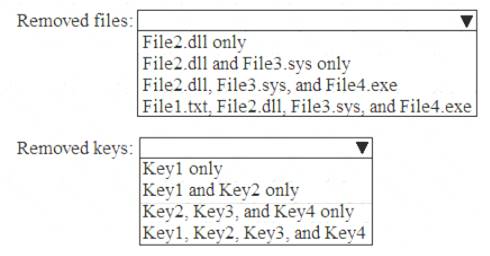
Solution:
References:
https://www.maketecheasier.com/what-system-restore-can-and-cannot-do-to-your-windows-system/ https://superuser.com/questions/343112/what-does-windows-system-restore-exactly-back-up-and-restore
Does this meet the goal?
Correct Answer:
A