- (Exam Topic 2)
A security analyst is investigating network issues between a workstation and a company server. The workstation and server occasionally experience service disruptions, and employees are forced to
reconnect to the server. In addition, some reports indicate sensitive information is being leaked from the server to the public.
The workstation IP address is 192.168.1.103, and the server IP address is 192.168.1.101. The analyst runs arp -a On a separate workstation and obtains the following results: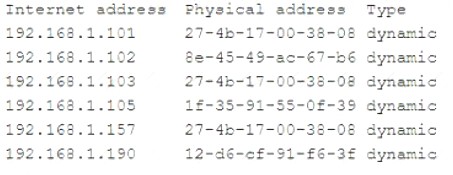
Which of the following is most likely occurring?
Correct Answer:
C
An on-path attack is a type of attack where an attacker places themselves between two devices (such as a
workstation and a server) and intercepts or modifies the communications between them. An on-path attacker can collect sensitive information, impersonate either device, or disrupt the service. In this scenario, the attacker is likely using an on-path attack to capture and alter the network traffic between the workstation and the server, causing service disruptions and data leakage.
- (Exam Topic 2)
A security administrator Is managing administrative access to sensitive systems with the following requirements:
• Common login accounts must not be used (or administrative duties.
• Administrative accounts must be temporal in nature.
• Each administrative account must be assigned to one specific user.
• Accounts must have complex passwords.
• Audit trails and logging must be enabled on all systems.
Which of the following solutions should the administrator deploy to meet these requirements?
Correct Answer:
C
The best solution to meet the given requirements is to deploy a Privileged Access Management (PAM) solution. PAM solutions allow administrators to create and manage administrative accounts that are assigned to specific users and that have complex passwords. Additionally, PAM solutions provide the ability to enable audit trails and logging on all systems, as well as to set up temporal access for administrative accounts. SAML, ABAC, and CASB are not suitable for this purpose.
- (Exam Topic 4)
An organization suffered numerous multiday power outages at its current location. The Chief Executive Officer wants to create a disaster recovery strategy to resolve this issue. Which of the following options offer low-cost solutions? (Select two).
Correct Answer:
BF
A generator and a UPS (uninterruptible power supply) are low-cost solutions that can provide backup power to an organization in case of a power outage. A generator is a device that converts mechanical energy into electrical energy, while a UPS is a device that provides battery power to a system when the main power source fails. A generator and a UPS can help the organization to maintain its operations and prevent data loss during a power outage.
- (Exam Topic 4)
A security engineer must deploy two wireless routers in an office suite Other tenants in the office building should not be able to connect to this wireless network Which of the following protocols should the engineer implement to ensure the strongest encryption?
Correct Answer:
B
WPA2 (Wi-Fi Protected Access 2) is a network security protocol that should be implemented to ensure the strongest encryption for a wireless network. WPA2 is an upgrade from the original WPA protocol, which was designed as a replacement for the older and less secure WEP protocol. WPA2 implements the mandatory elements of IEEE 802.11i standard, including CCMP, an AES-based encryption mode. WPA2 provides stronger security and data protection than WPS (Wi-Fi Protected Setup), WAP (Wireless Application Protocol), or HTTPS (Hypertext Transfer Protocol Secure)
- (Exam Topic 3)
A building manager is concerned about people going in and out of the office during non-working hours. Which of the following physical security controls would provide the best solution?
Correct Answer:
B
Badges are physical security controls that provide a way to identify and authenticate authorized individuals who need to access a building or a restricted area. Badges can also be used to track the entry and exit times of people and monitor their movements within the premises. Badges can help deter unauthorized access by requiring people to present a valid credential before entering or leaving the office. Badges can also help prevent tailgating, which is when an unauthorized person follows an authorized person through a door or gate. Badges can be integrated with other security systems, such as locks, alarms, cameras, or biometrics, to enhance the level of protection.