- (Topic 12)
Scanning for services is an easy job for Bob as there are so many tools available from the Internet. In order for him to check the vulnerability of company, he went through a few scanners that are currently available. Here are the scanners that he uses:
✑ Axent’s NetRecon (http://www.axent.com)
✑ SARA, by Advanced Research Organization (http://www-arc.com/sara)
✑ VLAD the Scanner, by Razor (http://razor.bindview.com/tools/)
However, there are many other alternative ways to make sure that the services that have been scanned will be more accurate and detailed for Bob.
What would be the best method to accurately identify the services running on a victim host?
Correct Answer:
B
By running a telnet connection to the open ports you will receive banners that tells you what service is answering on that specific port.
- (Topic 3)
You are manually conducting Idle Scanning using Hping2. During your scanning you notice that almost every query increments the IPID regardless of the port being queried. One or two of the queries cause the IPID to increment by more than one value. Why do you think this occurs?
Correct Answer:
A
If the IPID is incremented by more than the normal increment for this type of system it means that the system is interacting with some other system beside yours and has sent packets to an unknown host between the packets destined for you.
- (Topic 23)
You generate MD5 128-bit hash on all files and folders on your computer to keep a baseline check for security reasons?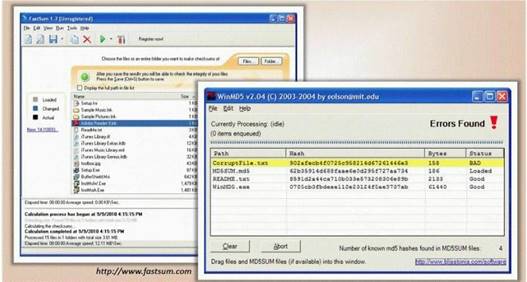
What is the length of the MD5 hash?
Correct Answer:
C
- (Topic 19)
Bob has set up three web servers on Windows Server 2003 IIS 6.0. Bob has followed all the recommendations for securing the operating system and IIS. These servers are going to run numerous e-commerce websites that are projected to bring in thousands of dollars a day. Bob is still concerned about the security of this server because of the potential for financial loss. Bob has asked his company’s firewall administrator to set the firewall to inspect all incoming traffic on ports 80 and 443 to ensure that no malicious data is getting into the network.
Why will this not be possible?
Correct Answer:
D
In order to really inspect traffic and traffic patterns you need an IDS.
- (Topic 3)
You are conducting an idlescan manually using HPING2. During the scanning process, you notice that almost every query increments the IPID- regardless of the port being queried. One or two of the queries cause the IPID to increment by more than one value. Which of he following options would be a possible reason?
Correct Answer:
B
If the IPID increments more than one value that means that there has been network traffic between the queries so the zombie is not idle.