- (Topic 3)
While attempting to discover the remote operating system on the target computer, you receive the following results from an nmap scan:
Starting nmap V. 3.10ALPHA9 ( www.insecure.org/nmap/
(The 1592 ports scanned but not shown below are in state: filtered) Port State Service
21/tcp open ftp 25/tcp open smtp 53/tcp closed domain 80/tcp open http 443/tcp open https
Remote operating system guess: Too many signatures match to reliably guess the OS.
Nmap run completed -- 1 IP address (1 host up) scanned in 277.483 seconds
What should be your next step to identify the OS?
Correct Answer:
D
Most people don’t care about changing the banners presented by applications listening to open ports and therefore you should get fairly accurate information when grabbing banners from open ports with, for example, a telnet application.
- (Topic 4)
Under what conditions does a secondary name server request a zone transfer from a primary name server?
Correct Answer:
A
Understanding DNS is critical to meeting the requirements of the CEH. When the serial number that is within the SOA record of the primary server is higher than the Serial number within the SOA record of the secondary DNS server, a zone transfer will take place.
- (Topic 19)
To scan a host downstream from a security gateway, Firewalking:
Correct Answer:
B
Firewalking uses a traceroute-like IP packet analysis to determine whether or not a particular packet can pass from the attacker’s host to a destination host through a packet-filtering device. This technique can be used to map ‘open’ or ‘pass through’ ports on a gateway. More over, it can determine whether packets with various control information can pass through a given gateway.
- (Topic 23)
Attackers target HINFO record types stored on a DNS server to enumerate information. These are information records and potential source for reconnaissance. A network administrator has the option of entering host information specifically the CPU type and operating system when creating a new DNS record. An attacker can extract this type of information easily from a DNS server.
Which of the following commands extracts the HINFO record?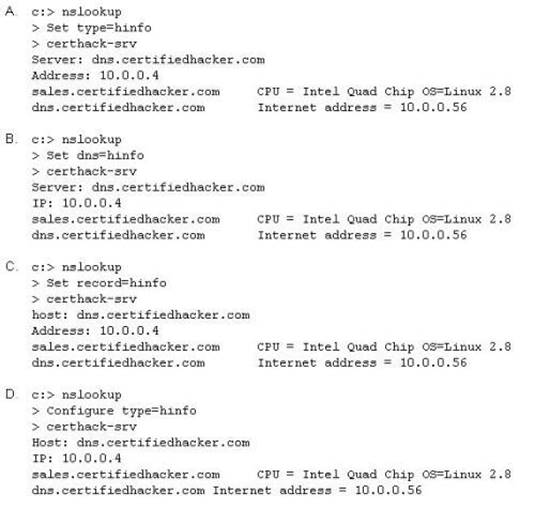
Correct Answer:
A
- (Topic 8)
Henry is an attacker and wants to gain control of a system and use it to flood a target system with requests, so as to prevent legitimate users from gaining access. What type of attack is Henry using?
Correct Answer:
B
Henry’s intention is to perform a DoS attack against his target, possibly a DDoS attack. He uses systems other than his own to perform the attack in order to cover the tracks back to him and to get more “punch” in the DoS attack if he uses multiple systems.