An engineer needs to implement QOS mechanism on customer's network as some applications going over the internet are slower than others. Which two actions must the engineer perform when implementing traffic shaping on the network in order to accomplish this task? (Choose two)
Correct Answer:
AD
Simulation 7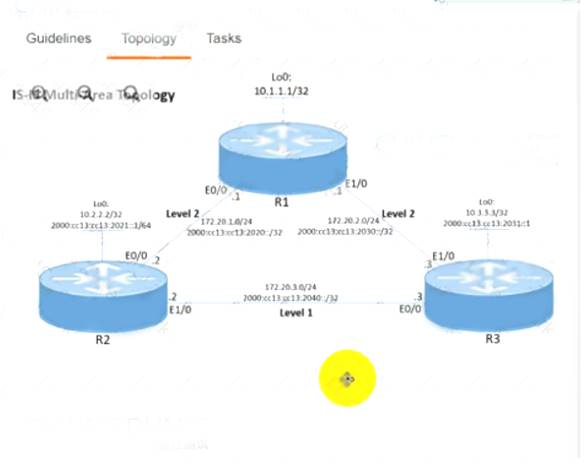
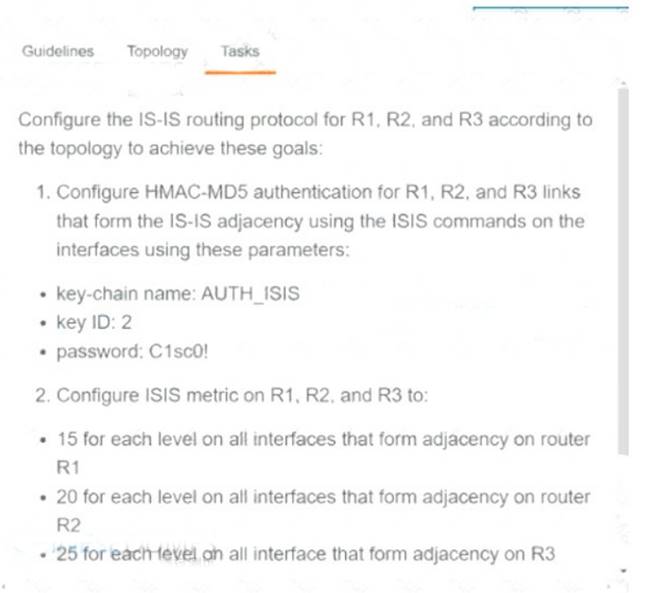
Solution:
R1
key chain AUTH_ISIS key 2
key-string C1sco! exit
int range et0/0 , et1/0
isis authen key-chain AUTH_ISIS ip isis
isis metric 15 Copy run start R2
key chain AUTH_ISIS key 2
key-string C1sco! exit
int range et0/0 , et1/0
isis authen key-chain AUTH_ISIS ip isis
isis metric 20 Copy run start R3
key chain AUTH_ISIS key 2
key-string C1sco! exit
int range et0/0 , et1/0
isis authen key-chain AUTH_ISIS ip isis
isis metric 25 Copy run start
Does this meet the goal?
Correct Answer:
A
Refer to the exhibit.
An engineer is securing a customer's network. Which command completes this configuration and the engineer must use to prevent a DoS attack?
Correct Answer:
C
Which two IS-IS parameters must match before two Level 2 peers can form an adjacency? (Choose two)
Correct Answer:
AD
A new PE router is configured to run OSPF as an IGP with LDP on all interfaces. The engineer is trying to prevent black holes after convergence when the PERSON device loses an LDP session with other PE routers. Which action must the engineer take to implement LDP session protection on a new PE router?
Correct Answer:
C