Which of the following can detect vulnerable third-parly libraries before code deployment?
Correct Answer:
C
Static analysis is a method of analyzing the source code or binary code of an application without executing
it. Static analysis can detect vulnerable third-party libraries before code deployment by scanning the code for references to known vulnerable libraries or versions and reporting any issues or risks12.
Impact analysis is a process of assessing the potential effects of a change on a system or service, such as performance, availability, security and compatibility. Impact analysis does not detect vulnerable third-party libraries before code deployment, but rather helps to evaluate and communicate the consequences of a change.
Dynamic analysis is a method of analyzing the behavior or performance of an application by executing it under various conditions or inputs. Dynamic analysis does not detect vulnerable third-party libraries before code deployment, but rather helps to identify any errors or defects that occur at runtime.
Protocol analysis is a method of examining the data exchanged between devices or applications over a network by capturing and interpreting the packets or messages. Protocol analysis does not detect vulnerable third-party libraries before code deployment, but rather helps to monitor and troubleshoot network communication.
During an investigation, an analyst discovers the following rule in an executive's email client: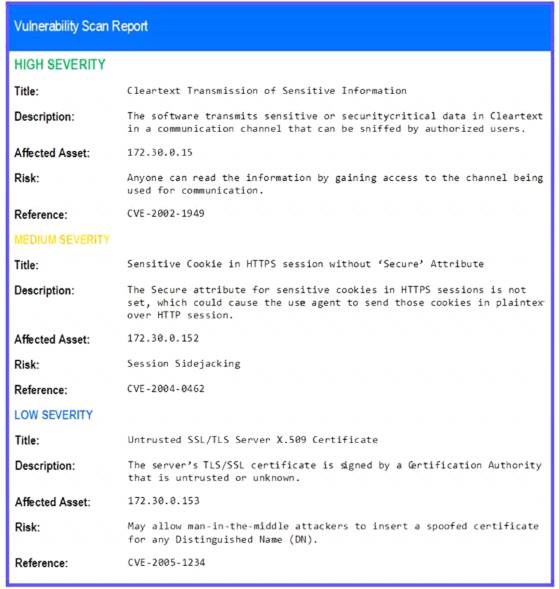
The executive is not aware of this rule. Which of the following should the analyst do first to evaluate the
potential impact of this security incident?
Correct Answer:
A
Checking the server logs to evaluate which emails were sent to <someaddress@domain,com> is the first action the analyst should do to evaluate the potential impact of this security incident. Server logs are records of events or activities that occur on a server, such as email transactions, web requests, or authentication attempts. Checking the server logs can help to determine how many emails were sent to <someaddress@domain,com>, when they were sent, who sent them, and what they contained. This can help to assess the scope and severity of the incident and plan further actions .
A developer downloaded and attempted to install a file transfer application in which the installation package is bundled with acKvare. The next-generation antivirus software prevented the file from executing, but it did not remove the file from the device. Over the next few days, more developers tried to download and execute the offending file. Which of the following changes should be made to the security tools to BEST remedy the issue?
Correct Answer:
D
Blocking the download of the file via the web proxy is the best change to make to the security tools to remedy the issue. A web proxy is a server that acts as an intermediary between a client and a web server, filtering or modifying requests and responses according to predefined rules1. Blocking the download of the file via the web proxy can prevent developers from accessing and executing the offending file that is bundled with adware. This can reduce the risk of infection or compromise of the developer workstations and improve their performance and security. Blacklisting the hash in the next-generation antivirus system (A) is not the best change to make to the security tools to remedy the issue. Blacklisting is a technique that involves blocking or denying access to known malicious or unwanted entities based on their identifiers, such as hashes, IP addresses, domains, etc2. Blacklisting the hash in the next-generation antivirus system can prevent developers from executing the offending file that is bundled with adware, but it does not prevent them from downloading it. This can still consume network bandwidth and disk space and expose developers to potential threats. Manually deleting the file from each of the workstations (B) is not the best change to make to the security tools to remedy the issue. Manually deleting the file from each of the workstations can remove the offending file that is bundled with adware, but it does not prevent developers from downloading it again. This can be a time-consuming and inefficient process that requires human intervention and coordination. Removing administrative rights from all developer workstations © is not the best change to make to the security tools to remedy the issue. Removing administrative rights from all developer workstations can limit developers’ ability to install or execute unauthorized or malicious applications, such as adware, but it does not prevent them from downloading them. This can also affect developers’ productivity and functionality by restricting their access to legitimate applications or settings.
References: 1: https://www.techopedia.com/definition/24771/technical-controls 2: https://www.techopedia.com/definition/25888/security-development-lifecycle-sdl
During an audit, several customer order forms were found to contain inconsistencies between the actual price of an item and the amount charged to the customer. Further investigation narrowed the cause of the issue to manipulation of the public-facing web form used by customers to order products. Which of the following would be the best way to locate this issue?
Correct Answer:
C
Implementing input validation is the best way to locate and prevent the issue of manipulation of the
public-facing web form used by customers to order products. Input validation is a technique that checks and filters any user input that is sent to an application before processing it. Input validation can help to ensure that the user input conforms to the expected format, length and type, and does not contain any malicious characters or syntax that may alter the logic or behavior of the application. Input validation can also reject or sanitize any input that does not meet the validation criteria .
A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results. The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Solution:
Does this meet the goal?
Correct Answer:
A