SIMULATION - (Topic 1)
Which of the following simulations would NOT be performed when testing a disaster recovery plan?
MISSING
Solution:
MISSING
Does this meet the goal?
Correct Answer:
A
- (Topic 2)
The FINAL phase of the accounting process involves the:
Correct Answer:
D
✑ Thefinal phase of the accounting process is generating financial statements (D), which summarize all accounting activities.
✑ Transactions (A), journal entries (B), and general ledger (C) occur earlier in the process.
References:
✑ Payroll Accounting Standards (Payroll.org)
- (Topic 2)
Workers?? compensation payments are excluded from gross income and employment taxes EXCEPT when the amounts received:
Correct Answer:
B
✑ Workers?? compensation benefits are tax-exempt if they are paid for work-related injuries or illnesses.
✑ If payments are received for non-work-related illnesses (B), they become taxable.
✑ Amounts that do not exceed federal or state limits (C & D) remain tax-exempt. References:
✑ IRS Publication 525 (Taxable and Nontaxable Income)
- (Topic 1)
Using the following information from a payroll register, calculate the tax deposit liability for the payroll.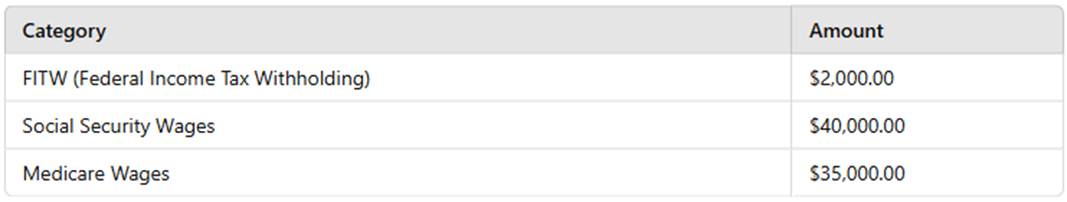
Correct Answer:
A
Comprehensive and Detailed Explanation:Thetax deposit liabilityincludesfederal income tax withholding (FITW), Social Security tax, and Medicare tax.
✑ Social Security Tax:
✑ Medicare Tax:
✑ Total Tax Deposit Liability: Thus, the correct answer isA. $7,975.00. Reference:
IRS Publication 15 – Employer's Tax Guide Payroll.org – Payroll Tax Calculation Best Practices
- (Topic 1)
Payroll staff should be aware of all of the following potential warning signs of a data breach EXCEPT:
Correct Answer:
C
Comprehensive and Detailed Explanation:Payroll security professionals must monitor forpotential payroll fraud or data breaches.
✑ A (Excessive security reset requests) Could indicate ahacker attempting
unauthorized access.
✑ B (Large payroll data requests) Could signalattempted data theft.
✑ D (Activity outside normal hours) Could be anexternal breach or insider threat.
✑ Option C (Reprinting a W-2) is NOT necessarily suspicious, as employees frequently request reprints during tax season.
Reference:
Payroll.org – Payroll Data Security Best Practices
IRS – Data Breach Prevention in Payroll